通常我们在使用Docker后会产生很多容器镜像,在这里我们搭建一个Harbor镜像仓库来存放容器镜像,使得拉取镜像时速度更快,更方便,这里会自签证书,在局域网内登录时可以避免登录显示不安全,从而减少编辑/etc/daemon.json文件
一、基础配置
1、更换软件源
#备份源文件
mkdir /etc/yum.repos.d/bak
mv /etc/yum.repos.d/* /etc/yum.repos.d/bak/ >>/dev/null 2>&1
#下载源文件
curl -L http://mirrors.aliyun.com/repo/Centos-7.repo -o /etc/yum.repos.d/CentOS-Base.repo
#清楚缓存并创建元数据
yum clean all && yum makecache2、安装基础软件
yum install vim epel-release.noarch yum-utils device-mapper-persistent-data lvm2 bash-completion wget tree -y
#设置hostname
hostnamectl set-hostname server
exec bash3、安装Docker
#添加Docker软件源
yum-config-manager --add-repo=http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
#安装Docker
yum install docker-ce docker-ce-cli -y
systemctl start docker
systemctl enable docker --now
#验证是否安装成功
[root@server ~]# docker info
Client: Docker Engine - Community
Version: 25.0.2
Context: default
Debug Mode: false
Plugins:
buildx: Docker Buildx (Docker Inc.)
Version: v0.12.1
Path: /usr/libexec/docker/cli-plugins/docker-buildx
compose: Docker Compose (Docker Inc.)
Version: v2.24.5
Path: /usr/libexec/docker/cli-plugins/docker-compose
Server:
Containers: 0
Running: 0
Paused: 0
Stopped: 0
Images: 0
Server Version: 25.0.2
Storage Driver: overlay2
Backing Filesystem: xfs
Supports d_type: true
Using metacopy: false
Native Overlay Diff: true
userxattr: false
Logging Driver: json-file
Cgroup Driver: cgroupfs
Cgroup Version: 1
Plugins:
Volume: local
Network: bridge host ipvlan macvlan null overlay
Log: awslogs fluentd gcplogs gelf journald json-file local splunk syslog
Swarm: inactive
Runtimes: io.containerd.runc.v2 runc
Default Runtime: runc
Init Binary: docker-init
containerd version: ae07eda36dd25f8a1b98dfbf587313b99c0190bb
runc version: v1.1.12-0-g51d5e94
init version: de40ad0
Security Options:
seccomp
Profile: builtin
Kernel Version: 3.10.0-862.el7.x86_64
Operating System: CentOS Linux 7 (Core)
OSType: linux
Architecture: x86_64
CPUs: 4
Total Memory: 3.685GiB
Name: localhost.localdomain
ID: 3e8c1b2a-50e1-473c-b280-764df30bf4ec
Docker Root Dir: /var/lib/docker
Debug Mode: false
Experimental: false
Insecure Registries:
127.0.0.0/8
Live Restore Enabled: false4、安装docker-compose
wget "https://github.com/docker/compose/releases/download/v2.24.5/docker-compose-$(uname -s)-$(uname -m)" -O /usr/local/bin/docker-compose
#增加执行权限
chmod a+x /usr/local/bin/docker-compose
[root@server ~]# docker-compose version
Docker Compose version v2.24.55、内核升级
我这里为了后续软件支持需要升级内核,如不想升级内核可直接跳过此步
#查看内核
uname -sr1、导入公钥
rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
rpm -Uvh https://www.elrepo.org/elrepo-release-7.el7.elrepo.noarch.rpm2、加载elrepo-kernel元数据
yum --disablerepo="*" --enablerepo="elrepo-kernel" repolist
kernel-lt和kernel-ml二者的区别:
kernel-ml软件包是根据Linux Kernel Archives的主线稳定分支提供的源构建的。 内核配置基于默认的RHEL-7配置,并根据需要启用了添加的功能。 这些软件包有意命名为kernel-ml,以免与RHEL-7内核发生冲突,因此,它们可以与常规内核一起安装和更新。kernel-lt包是从Linux Kernel Archives提供的源代码构建的,就像kernel-ml软件包一样。 不同之处在于kernel-lt基于长期支持分支,而kernel-ml基于主线稳定分支。在
ELRepo中有两个内核选项,一个是kernel-lt(长期支持版),一个是kernel-ml(主线最新版本),采用长期支持版本(kernel-lt),会更加稳定。
3、查看可用内核版本
[root@server ~]# yum --disablerepo="*" --enablerepo="elrepo-kernel" list available | sort -c
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* elrepo-kernel: hkg.mirror.rackspace.com
Available Packages
kernel-ml.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-tools.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-tools-libs.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-tools-libs-devel.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-headers.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-doc.noarch 6.7.3-1.el7.elrepo elrepo-kernel
kernel-ml-devel.x86_64 6.7.3-1.el7.elrepo elrepo-kernel
kernel-lt-tools.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
kernel-lt-tools-libs.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
kernel-lt-tools-libs-devel.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
kernel-lt-headers.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
kernel-lt-doc.noarch 5.4.268-1.el7.elrepo elrepo-kernel
kernel-lt-devel.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
perf.x86_64 5.4.268-1.el7.elrepo elrepo-kernel
python-perf.x86_64 5.4.268-1.el7.elrepo elrepo-kernel4、安装长期支持版本
yum --enablerepo="elrepo-kernel" install kernel-lt 查看当前系统下可用内核
[root@server ~]# awk -F\' '$1=="menuentry " {print $2}' /etc/grub2.cfg
CentOS Linux (5.4.268-1.el7.elrepo.x86_64) 7 (Core)
CentOS Linux (3.10.0-862.el7.x86_64) 7 (Core)
CentOS Linux (0-rescue-4e37109fc2c64b78804e7b0263d94b67) 7 (Core)5、创建内核配置
[root@server ~]# grub2-mkconfig -o /boot/grub2/grub.cfg
Generating grub configuration file ...
Found linux image: /boot/vmlinuz-5.4.268-1.el7.elrepo.x86_64
Found initrd image: /boot/initramfs-5.4.268-1.el7.elrepo.x86_64.img
Found linux image: /boot/vmlinuz-3.10.0-862.el7.x86_64
Found initrd image: /boot/initramfs-3.10.0-862.el7.x86_64.img
Found linux image: /boot/vmlinuz-0-rescue-4e37109fc2c64b78804e7b0263d94b67
Found initrd image: /boot/initramfs-0-rescue-4e37109fc2c64b78804e7b0263d94b67.img
done
[root@server ~]#6、设置开机加载新内核
grub2-set-default 0 重启并验证
reboot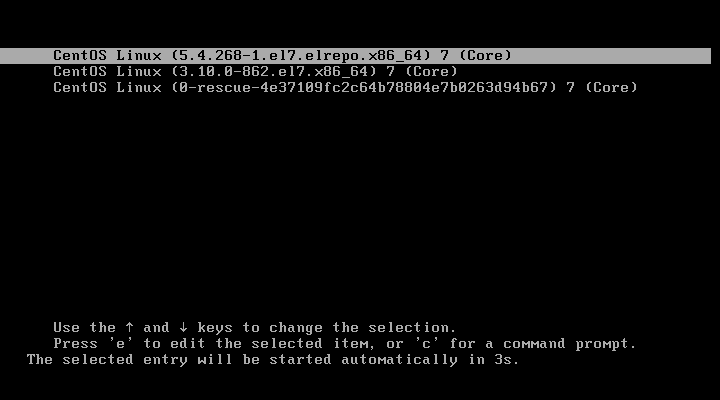
[root@server ~]# uname -sr
Linux 5.4.268-1.el7.elrepo.x86_64
[root@server ~]# 二、自签证书
以下用到域名的地方自行替换成自己的域名我的域名是:iw.harbor
1、创建ca证书私钥
[root@server /]# mkdir /data/cert && cd /data/cert
[root@server cert]# openssl genrsa -out ca.key 4096
Generating RSA private key, 4096 bit long modulus
........................................................................................++
..............++
e is 65537 (0x10001)2、创建ca证书
openssl req -x509 -new -sha512 -days 3650 -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=iw.harbor" -key ca.key -out ca.crt3、生成域名证书
1、生成私钥
[root@server cert]# openssl genrsa -out iw.harbor.key 4096
Generating RSA private key, 4096 bit long modulus
.............................................................................++
...........................................++
e is 65537 (0x10001)2、生成证书签名请求(CSR)
openssl req -sha512 -new -subj "/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=iw.harbor" -key iw.harbor.key -out iw.harbor.csr3、生成x509 v3扩展文件
这里有两种方式,如果是域名则选择第一种,IP则选择第二种
################################
#域名访问,注意修改域名等信息
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1=iw.harbor #xxxx.yourdomain 加上二级域名
DNS.2=harbor #yourdomain
DNS.3=server #hostname
EOF
################################
#下面是第二种(IP访问)注意IP更换为自己的服务器IP
cat > v3.ext <<-EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth
subjectAltName = IP:192.168.200.147
EOF4、生成主机证书
使用上面生出的v3.ext证书生出harbor主机证书
[root@server cert]# openssl x509 -req -sha512 -days 3650 -extfile v3.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in iw.harbor.csr -out iw.harbor.crt
Signature ok
subject=/C=CN/ST=Beijing/L=Beijing/O=example/OU=Personal/CN=iw.harbor
Getting CA Private Key5、提供证书给Harbor和Docker
1、转换crt为cert,提供给Docker守护进程
Docker守护进程会将.crt文件解释为CA证书,并将.cert文件解释为客户端证书
openssl x509 -inform PEM -in iw.harbor.crt -out iw.harbor.certcp iw.harbor.crt /etc/pki/ca-trust/source/anchors/iw.harbor.crt 2、创建文件夹并将服务器证书、密钥和CA文件复制到Harbor主机的Docker certificate文件夹中
mkdir -p /etc/docker/certs.d/iw.harbor/
cp iw.harbor.cert iw.harbor.key ca.crt /etc/docker/certs.d/iw.harbor/ 最终Docker目录结构如下
[root@server cert]# tree /etc/docker/certs.d/
/etc/docker/certs.d/
└── iw.harbor
├── ca.crt
├── iw.harbor.cert
└── iw.harbor.key
1 directory, 3 files3、重启Docker
systemctl restart docker三、部署Harbor
1、下载harbor离线安装包
wget https://github.com/goharbor/harbor/releases/download/v2.10.0/harbor-offline-installer-v2.10.0.tgz1、解压文件
tar -zxvf harbor-offline-installer-v2.10.0.tgz2、修改Harbor配置文件
cd harbor/
#复制配置文件
cp harbor.yml.tmpl harbor.yml
vim harbor.yml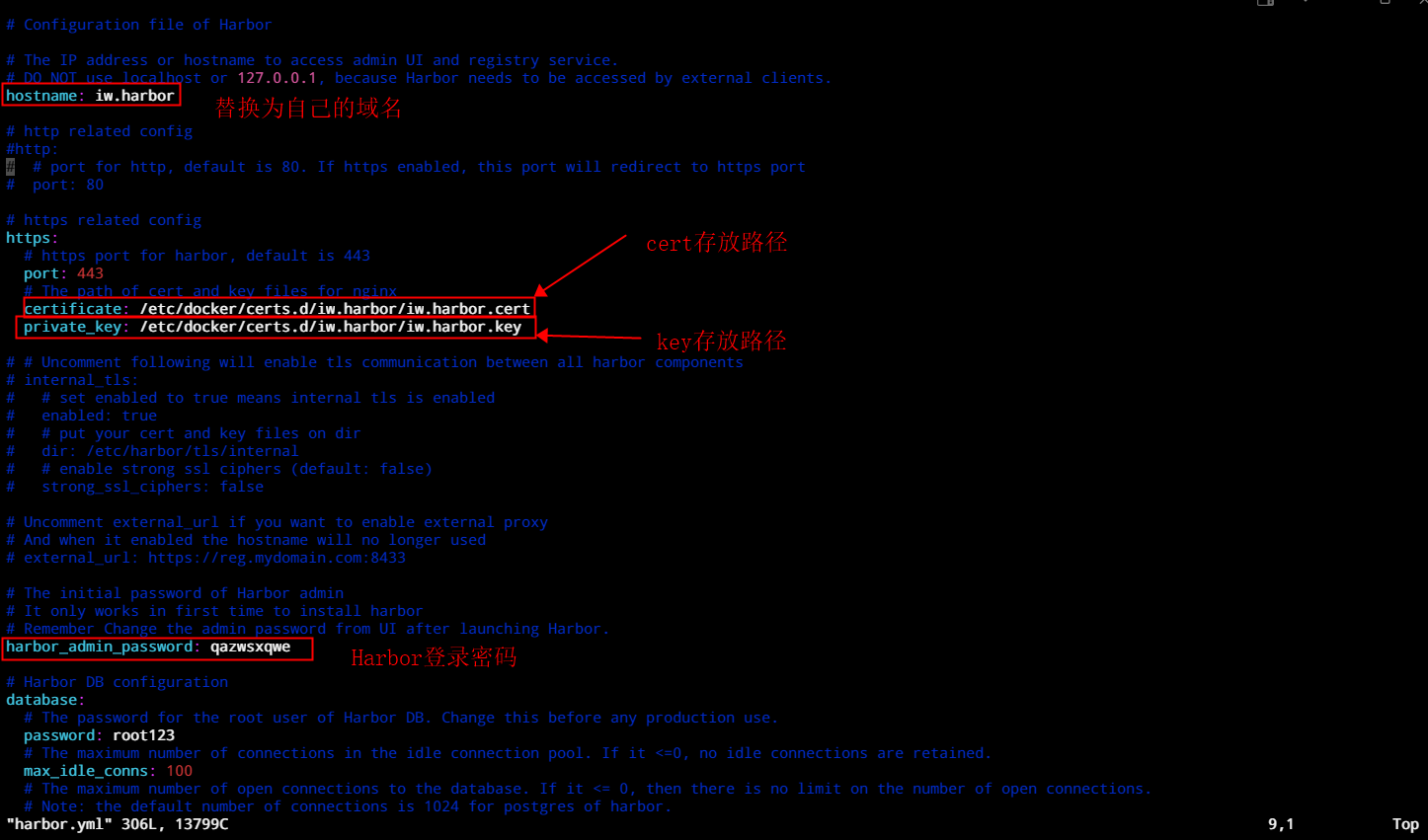
3、运行脚本部署harbor
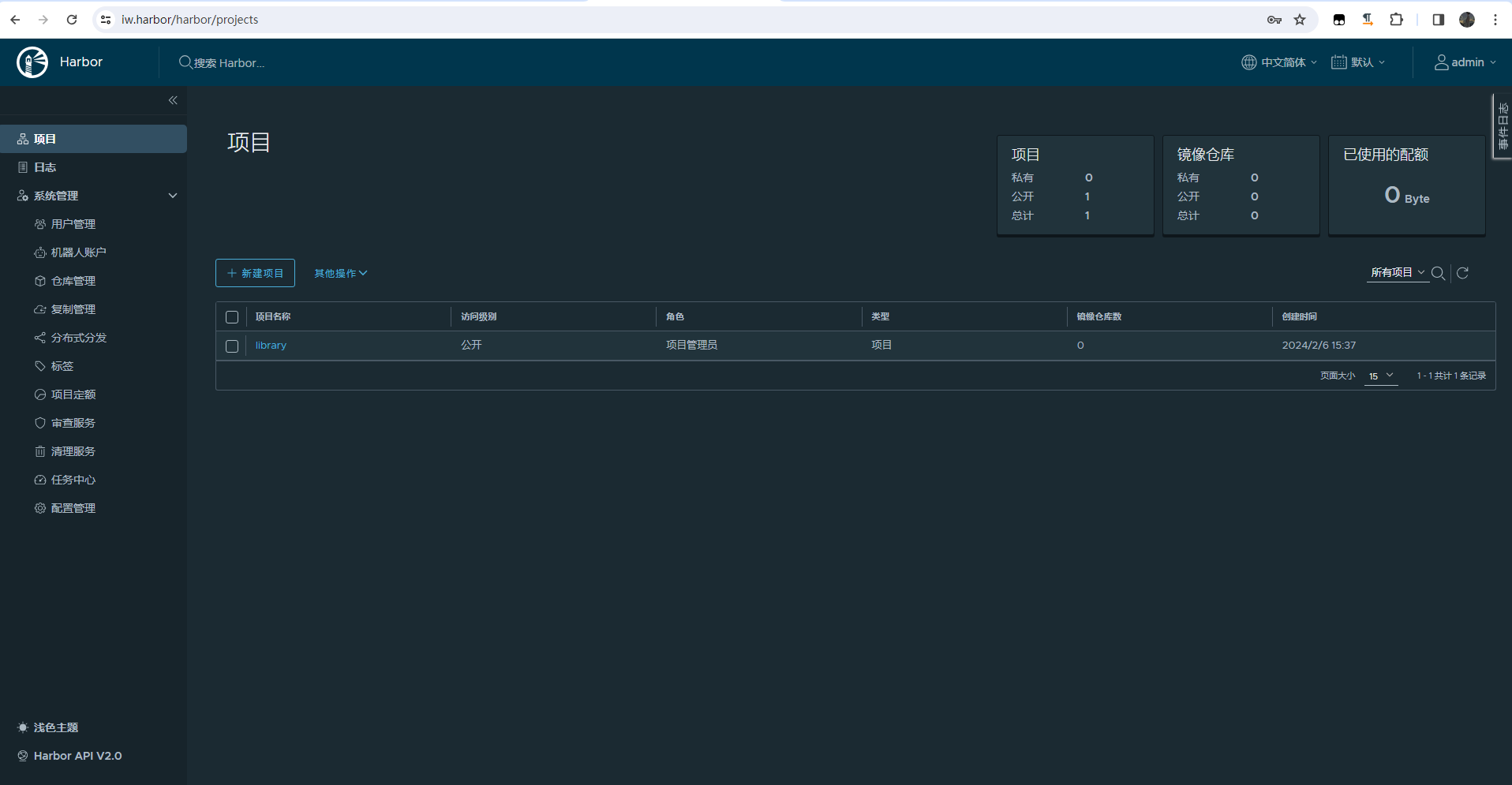
./install.sh完成后出现以下界面

用浏览器访问还是会出现不安全提示,可以把CA证书下载到需要访问该仓库的服务器手动导入浏览器
可以看到导入证书后,浏览器url左侧不再提示不安全等字样